Lossless & Bridge Network Partnership Upgrade


Lossless & Bridge Network partnership upgrade has been announced. Last year, Bridge Network formed a partnership with Lossless.
Bridge Network’s bridge has been launched onto the mainnet and it has Lossless Protocol implemented too. What this means is that token owners bridging their tokens to different chains via Bridge Network will have the opportunity to secure them with Lossless Protocol.
Moreover, hacks have been a familiar occurrence in the bridging world due to a lack of effective security measures.
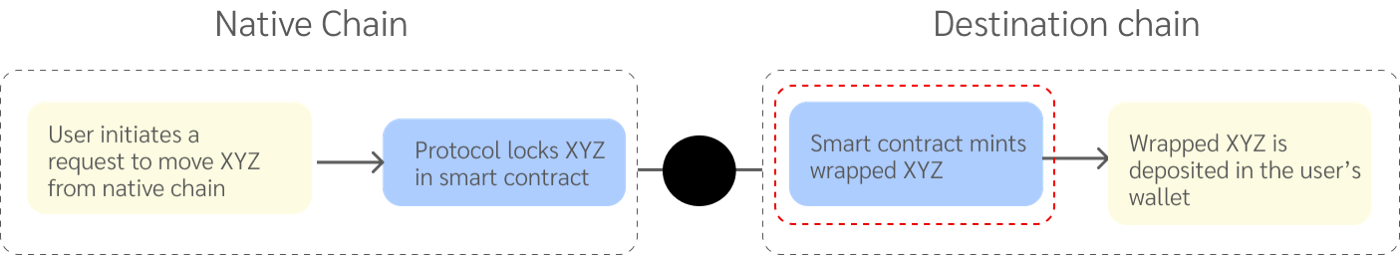
The asset is locked on its native chain and a wrapped version is minted on the destination chain. The smart contract that mints the wrapped asset is generally where exploits occur as hackers attempt to mint more tokens than they lock.

BRIDGE NETWORK GOALS
Furthermore, Bridge Network‘s goal is to set a new standard by working with projects such as Lossless to bring security and trust to the bridging world. Tokens wrap in the LSS standard will enable Lossless security parameters for the bridged tokens.
Moreover, the Lossless team is excited about Bridge Network’s progress and about the opportunity, this presents to the crypto industry. In addition, many more cryptocurrencies will now have the chance to acquire higher security standards.
ABOUT Bridge Network
Bridge Network is the ecosystem’s first cross-chain hub. Provides all the tools for users and creators to seamlessly transact between blockchains. Additionally, the bridge toolkit currently contains 4 tools, all connected to the core of the Bridge Network protocol. Users can move an asset (crypto or NFT) cross-chain, trade multiple assets cross-chain, as well as create their own bridge with no development experience.
ABOUT Lossless
Lossless protocol implements an additional layer of blockchain transaction security for ERC-20 standard tokens, mitigating the financial impact of smart contract exploits and private key theft. Lossless protocol utilizes community-driven threat identification tools and a unique stake-based reporting system to identify suspicious transactions, providing real-time protection.
RESOURCES
Medium




